About Sapphire
(excerpted from CERT Advisory CA-2003-04 MS-SQL Server Worm) The worm targeting SQL Server computers is self-propagating malicious code that exploits the vulnerability described in VU#484891 (CAN-2002-0649). This vulnerability allows for the execution of arbitrary code on the SQL Server computer due to a stack buffer overflow.
Once the worm compromises a machine, it will try to propagate itself. The worm will craft packets of 376-bytes and send them to randomly chosen IP addresses on port 1434/udp. If the packet is sent to a vulnerable machine, this victim machine will become infected and will also begin to propagate. Beyond the scanning activity for new hosts, the current variant of this worm has no other payload.
Activity of this worm is readily identifiable on a network by the presence of 376-byte UDP packets. These packets will appear to be originating from seemingly random IP addresses and destined for port 1434/udp.
Technical Report
A technical report on Sapphire is available, titled "The Spread of the Sapphire/Slammer Worm" authored by David Moore (CAIDA), Vern Paxson (ICIR & LBNL), Stefan Savage (UCSD CSE), Colleen Shannon (CAIDA), Stuart Staniford (Silicon Defense), Nicholas Weaver (Silicon Defense & UC Berkeley EECS). The technical report is available at https://catalog.caida.org/paper/2003_sapphire/
Support for this work was provided by NSF, DARPA, Silicon Defense, Cisco Systems, AT&T, NIST, and CAIDA members.
Animation
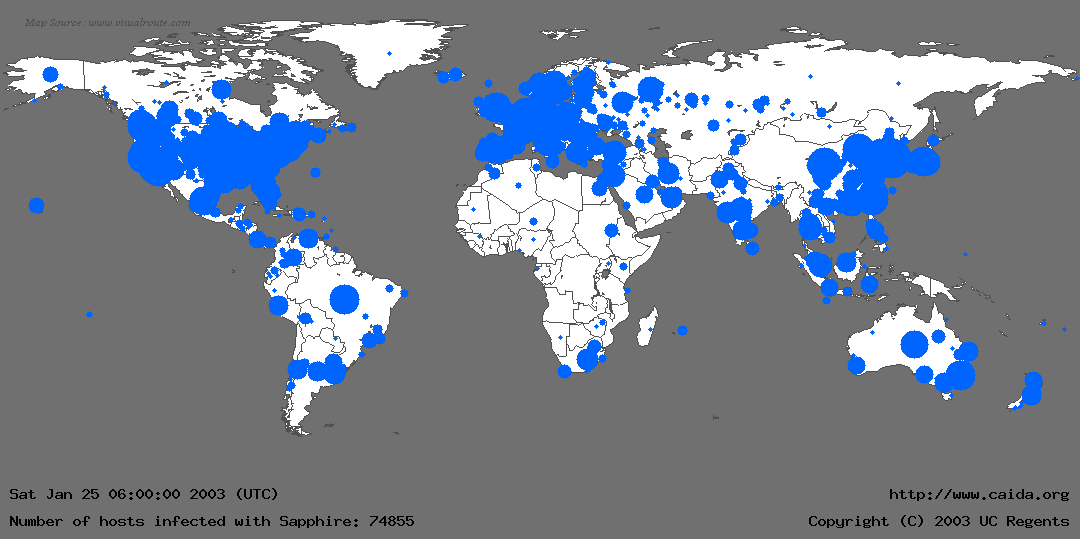
A before-and-after animation showing the number of infected Sapphire hosts in a half-hour period between 05:29 UTC and 06:00 UTC.
Thanks to Ryan Koga (CAIDA) and Jeffery Brown (UCSD CSE) for producing this animation of the worm spread.

