Place: Weaver Conference Center, Malamud Room, Institute of the Americas
UC San Diego Campus, La Jolla, CA
NDN Retreat 2015: How to Develop Secure Named Data Applications
We are pleased to announce the NDN 2015 Retreat: an opportunity to discuss the application environments, the NDN software platform and testbed, and focus on some specific areas such as security. This 2-day meeting will be hosted by UC San Diego in the first week of February 2015.
The primary goals of the retreat are:
- Gain new insights and ideas for NDN trust and security mechanism in the context of the network environments
- Find new design directions for the pilot applications in the proposed network environments
- See active involvement by all attendees
We wish to focus our interactions and discussions on making problems of security within the targeted NDN-NP application environments concrete and to find and flesh out application specific security problems. We hope to focus on student interaction and new ideas related to NDN NP applications in a retreat-style setting.
The NDN project uses current and future applications to drive the development and deployment of the architecture and its supporting modules, to test prototype implementations, and to encourage an iterative cycle of hands-on experimentation, evaluation, and design. So, we particularly encourage attendees to prepare in advance of the retreat: install all prerequisites for developing and running NDN applications.
Registration for this meeting is closed.
Recommended Reading List
- Recommended reading: NDN Network Environment: Enterprise Building Automation and Monitoring Systems
- Recommended reading: NDN Network Environment: Open mHealth
- Schematized Trust in NDN, slides by Van Jacobson (Google) at FIA-NP meeting, May 2014
- Network Environment References, listed in order of priority: (download via Dropbox link)
- Open mHealth Architecture: An Engine for Health Care Innovation. Sim & Estrin, 2010. (Open mHealth)
- Securing Building Management Systems Using Named Data Networking. Shang et al, 2014. (EBAMS)
- Self-Protecting Electronic Medical Records Using Attribute-Based Encryption. Akinyele et al, 2010. (Open mHealth) (New)
- Guide to Industrial Control Systems (ICS) Security. Stouffer et al, 2013, chaps 2 & 3. (EBAMS)
- PEIR, the Personal Environmental Impact Report, as a Platform for Participatory Sensing Systems Research. Mun et al, 2009. (Open mHealth)
- BOSS: Building Operating System Services. Dawson-Haggerty et al, 2013 and http://project-haystack.org/. (EBAMS)
- Healthcare in the pocket: Mapping the space of mobile-phone health interventions. Klasnja et al, 2014. (Open mHealth)
- Do-it-yourself Healthcare: The current landscape, prospects and consequences. Carrera et al, 2013. (Open mHealth)
- Ohmage: A General and Extensible End-to-End Participatory Sensing Platform. Tangmunarunkit et al, 2014. (Open mHealth)
Agenda
Instructions are provided to Access retreat materials via NDN.
February 4 (Wednesday)
- 17:30 - 19:00 (optional) Afternoon setup and configuration
- Local network configuration and room setup
- Demo preparation
February 5 (Thursday)
- 08:00 - 09:00 breakfast
- 09:00 - 09:30 Introductions: logistics, goals for the retreat
- 09:30 - 12:30 Discussion: security challenges for network environments (max. 10 mins per intro talk)
Existing mechanisms: introduction and application to Network Environments
Outcome: design directions for network environment pilot apps- Naming and Trust Models
- Yingdi Yu (UCLA), Packet validation & certificates
- James Kasten (University of Michigan), Let's Encrypt: Applications for NDN
- Discussion questions:
- What are the fundamental trust models for each network environment, and can they be mapped to well-studied models where possible?
- What is the appropriate relationship between data and key namespaces for each network environment?
- How should trust and security models impact namespace design in terms of tree organization, data naming granularity, etc.?
- What are critical semantics of each network environment, especially in terms of trust, that should be expressed in the names?
10:30 - 11:00 break
- Confidentiality
- Wentao Shang (UCLA), NDN-BMS Security: Requirements and Solution
- Haitao Zhang (UCLA), Attribute-based Encryption for NDNEx (also see related paper 1, paper 2, paper 3)
- Steve DiBenedetto (Colorado State University), ANDaNA: Onion Routing for NDN (Powerpoint version)
- Discussion questions:
- How should we encrypt payloads? Can all payloads be encrypted? What are the implications of payload encryption for other NDN goals (e.g., efficient caching)?
- How can we encrypt portions of the namespace to prevent the names themselves from leaking information?
- Where in the stack should confidentiality be implemented? Should it be added to the packet format? As a layer above? Left to applications?
- What are the tradeoffs of confidentiality protection in terms of complexity, performance, etc.? How can we best support advanced forms of crypto (e.g., ABE) for applications that benefit from them?
- Securing NFN-style data flow processing
- Christian Tschudin (University of Basel), Securing NFN-style data flow processing
- Discussion questions:
- How can signatures be verified far in the future? What are the right semantics for this--for instance, what if the keys are expired or compromised? Would a third-party notary or timestamping service help?
- What requirements do different applications impose on the signature mechanism, in terms of delegation, revocation, granularity, etc.?
- What are the tradeoffs of integrity protection in terms of complexity, performance, etc.? Who should set the points on these tradeoffs, publishers or consumers?
- Naming and Trust Models
- 12:30 - 14:00 Working lunch / Lightning talks
- Tarek Abdelzaher (University of Illinois at Urbana-Champaign), InfoMax: An Auto-summarizing Information Delivery Protocol
- Yingdi Yu (UCLA), Secure Multicast Interest in ChronoSync
- John DeHart (Washington University in St. Louis), NDN testbed status update
- Haowei Yuan (Washington University in St. Louis), Reliably Scalable Name Prefix Lookup
- Wentao Shang (UCLA), BMS-Repo Design Choices
- Daniel Zappala (Brigham Young University), Middleware for Certificate-based Authentication
- 14:30 - 16:00 Second round of security challenges discussion
Outcome: Identify breakout groups to pursue design directions for pilot applications emerging from today's discussion- Authorization and Integrity
- Dustin O'Hara (UCLA), User Experience Research & Design for NDN mHealth & Identity Manager App (also see related paper)
- Discussion questions:
- How do clients find the correct public key for a particular entity?
- How do clients verify whether a given public key is allowed to publish to a particular namespace? How can this authority be granted, delegated, revoked, etc.?
- How do clients obtain keys to decrypt particular content? How can this ability be granted, delegated, revoked, etc.?
- How can authorization be separated from identity in applications that require anonymity or other forms of privacy protection?
- Authorization and Integrity
- 16:00 - 16:30 break
- 18:00 - 19:00 Demos
- Peter Gusev (UCLA REMAP), NdnCon / ndnrtc, including setup help
- Zhehao Wang (UCLA REMAP), ndnfs, including setup help
- Jeff Thompson (UCLA REMAP), Crypto.subtle speedups to NDN-JS
- Jeff Burke (UCLA REMAP), UCLA BMS access
- 18:00 - 20:00 Reception on-site / Discussion between project PIs on various issues: IRTF, consortium, other external affairs
February 6 (Friday)
- 08:00 - 09:00 breakfast
- 09:00 - 09:30 Review of previous day, guiding breakout sessions
- Jeff Burke (UCLA REMAP), NDN NP Network Environments (really short) Recap
- 09:30 - 11:30 Breakout session: explore/expand on specific netenv pilot application and design directions
- Data authentication/integrity approach, with sample policy expressions in Y & V languages
- Need to express, not reinvent the trust models. BMS is hierarchical in two namespaces: data and users/principles. Open mHealth users each assemble a collection of components from an "app-style ecosystem" (what model there?) and trust each other in a social network style ecosystem, but with granular sharing
- What is the appropriate relationship between data and key namespaces for each network environment?
- How should trust and security models impact namespace design in terms of tree organization, data naming granularity, etc.?
- What are critical semantics of each network environment, especially in terms of trust, that should be expressed in the names?
- How do we express trust models at the app level (now) for moving on these sample apps?
- Need to express, not reinvent the trust models. BMS is hierarchical in two namespaces: data and users/principles. Open mHealth users each assemble a collection of components from an "app-style ecosystem" (what model there?) and trust each other in a social network style ecosystem, but with granular sharing
- Data confidentiality/encryption based access control approach
- Granular and expressive approach to confidentiality is important, without overcomplicating things. Multiple spheres of selective access seem important in both apps - based on data source/type, temporal range, consumer group membership. Eventually need to solve M2M (data flow) authentication, not always human in the loop
- How should we encrypt payloads? Can all payloads be encrypted? What are the implications of payload encryption for other NDN goals (e.g., efficient caching?)
- How can we encrypt portions of the namespace to prevent the names themselves from leaking information?
- What are the tradeoffs of confidentiality protection in terms of complexity, performance, etc? How can we best support advanced forms of crypto (e.g., ABE) for applications that benefit from them?
- Granular and expressive approach to confidentiality is important, without overcomplicating things. Multiple spheres of selective access seem important in both apps - based on data source/type, temporal range, consumer group membership. Eventually need to solve M2M (data flow) authentication, not always human in the loop
- Adapting "Let's Encrypt" mechanism to bootstrapping trust in devices and other principals
- For EBAMS, focus on actual BMS deployment context, not generic IoT or Smart Home context. (That's important but not our target in the netenv yet). For Open mHealth, focus on user-initiated, user-centric models per the use case in the appendix
- What can be completely automated? When should the human be in the loop, and how?
- How is the process/policy for bootstrapping articulated (whether in name and conventions or policies?)
- How can we create visibility into the establishment of trust when needed?
- For EBAMS, focus on actual BMS deployment context, not generic IoT or Smart Home context. (That's important but not our target in the netenv yet). For Open mHealth, focus on user-initiated, user-centric models per the use case in the appendix
- How to approach key storage (both systems and namespace problems)
- Again, focus on actual deployment context and scale for BMS. For Open mHealth, consider the nature of the ecosystem that's proposed, then design for the sample apps, which include just a few components.
10:30 - 11:00 break
- Data authentication/integrity approach, with sample policy expressions in Y & V languages
- 11:30 - 12:30 Discussion of results from breakout session
- 12:30 - 13:30 lunch
- 13:30 - 15:00 Discussion of pending architectural issues
- Beichuan Zhang (University of Arizona), Some Technical/Architectural Issues
- Lan Wang (University of Memphis), NDN Routing Security
- 15:00 - 16:00 Wrap-up: Concluding discussion, plan for FIA meeting, etc.
- Hotel
For this meeting, all attendees are still expected to make their own hotel reservations and transportation arrangements from their hotels to the meeting. The Estancia La Jolla hotel is also right across the street from the retreat location. For CAIDA's list of recommended local hotels including UC San Diego group rates and shuttle availability, see the most recent Recommended Hotels list (PDF). Contact the hotel directly for hotel shuttle schedules (if available) to the Institute of the Americas on UC San Diego Campus.
- Transportation options
- Shuttle to Hotels: SuperShuttle can be arranged to shuttle to UC San Diego campus or your hotel.
- Taxis: Yellow Cab of San Diego. A GPS pointed at "9855 International Ln, La Jolla, CA" should take you close enough to see the signs the Institute of Americas and the Weaver Center.
- Car rental: Available at the airport
- Meeting Room
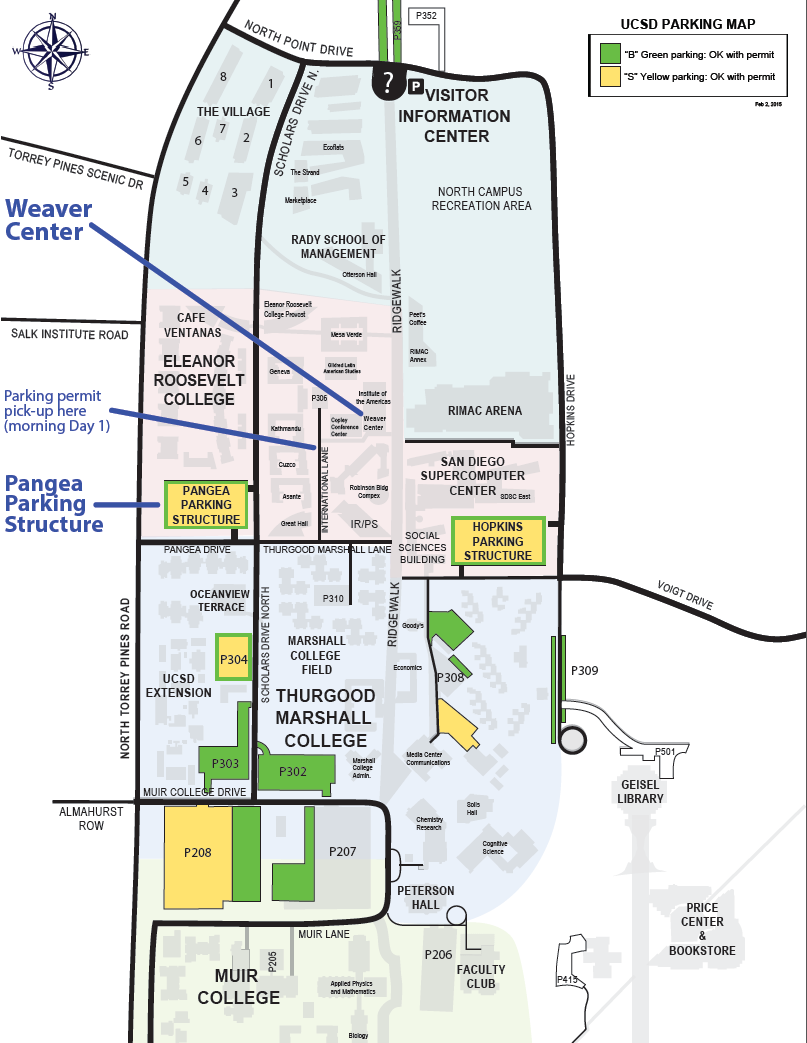
The retreat will be held in the Weaver Center, Malamud Room at the Institute of the Americas on the University of California San Diego campus. For directions to the Institute of the Americas, visit their website at http://www.iamericas.org/en/ - Parking
Parking Permits: Upon arrival, check in at the small parking strip (P306) on International Lane leading to the Institute of the Americas plaza before the start of the meeting on Day 1. We will give you a parking permit and instructions how to mark it, and point you to the Pangea Parking Structure for parking.
A campus map for the NDN retreat shows where the permits will be distributed, the parking structure, and the Weaver Center where the meeting will be held.
Parking permits for the subsequent day will be provided at the end of Day 1, just prior to the Reception.
Local Arrangements / Getting to UC San Diego
For transportation concerns, general questions and help, contact ndn-registration at caida.org
- An Endorsement-based Key Management System for Decentralized NDN Chat Application. Yingdi Yu, Alexander Afanasyev, Zhenkai Zhu, and Lixia Zhang. NDN, Technical Report NDN-0023, Revision 1: July 22, 2014.
- Securing Building Management Systems Using Named Data Networking by Wentao Shang, Qiuhan Ding, Alessandro Marianantoni, Jeff Burke, and Lixia Zhang IEEE Network, vol. 28, no. 3, pp. 50-56, May/June 2014.
- A Lightweight Mechanism for Detection of Cache Pollution Attacks in Named Data Networking by Mauro Conti, Paolo Gasti and Marco Teoli. Elsevier Journal on Computer Networks (COMNET), Special Issue on Mobile Computing for Content/Service Oriented Networking Architecture (2013)
- DoS & DDoS in Named Data Networking by Paolo Gasti, Gene Tsudik, Ersin Uzun, and Lixia Zhang. Proceedings of ICCCN 2013.
- Interest Flooding Attack and Countermeasures in Named Data Networking by A. Afanasyev, P. Mahadevan, I. Moiseenko, E. Uzun, and L. Zhang Proceedings of IFIP Networking 2013.
- Privacy in Content-Oriented Networking: Threats and Countermeasures by A. Chaabane, E. De Cristofaro, M. Kafaar, E. Uzun ACM SIGCOMM Computer Communication Review (CCR), July 2013.
- Cache Privacy in Named Data Networking by Gergely Acs, Mauro Conti, Paolo Gasti, Cesar Ghali and Gene Tsudik. International Conference on Distributed Computing Systems (ICDCS 2013), July 2013
- Security Evaluation of a Control System Using Named Data Networking by Victor Perez, Mevlut Turker Garip, Silas Lam, and Lixia Zhang Eighth Workshop on Secure Network Protocols (NPSec), October 2013
- Securing Instrumented Environments over Content-Centric Networking: the Case of Lighting Control by J. Burke, P. Gasti, N. Nathan, and G. Tsudik. Proceedings of IEEE INFOCOMM 2013 NOMEN Workshop, April 2013.
- Deploying Key Management on NDN Testbed by Chaoyi Bian, Zhenkai Zhu, Alexander Afanasyev, Ersin Uzun, and Lixia Zhang NDN Technical Report NDN-0009, Revision 2, February, 2013.
- Authenticated Lighting Control Using Named Data Networking by Jeff Burke, Alex Horn, and Alessandro Marianantoni NDN Technical Report NDN-0011, October, 2012.
- ANDaNA: Anonymous Named Data Networking Application by S. DiBenedetto, P. Gasti, G. Tsudik, E. Uzun. 19th Annual Network & Distributed System Security Symposium, February 2012.
- A New Approach to Securing Audio Conference Tools by Z. Zhu, P. Gasti, Y. Lu, J. Burke, V. Jacobson, L. Zhang Asia Workshop on Future Internet Technologies, November 2011.
- Securing Network Content by D. Smetters, V. Jacobson PARC Tech Report, October 2009.