CodeRed Worm Infections in 24.0.0.0/8 on July 19, 2001
Background
A "worm" is a computer program purposefully written to replicate itself from machine to machine across a network--or a network of networks like the Internet. Worms are hostile programs by definition since they commandeer the resources (even if only a small amount) of host machines and networks without permission. They typically spread by exploiting weaknesses or outright flaws in the design or implementation of complex software systems like web servers. Because they are programs actually running on infected hosts, and often with elevated privileges, it only takes malicious intent to create a worm that causes irrevocable and significant damage to host machines. They also have the potential to serve as agents in a distributed denial-of-service (DDoS) attack.
CodeRed is the name of a worm (and variants) that spread with alarming rapidity on July 19, 2001. Beginning on the morning of July 19th, UTC, a random seed variant infected over 359,000 machines in a 14 hour period. It was also programmed to launch a denial-of-service attack against www.whitehouse.gov. For further details, see CAIDA's analysis of the spread of CodeRed.
Description
Each host on the Internet has an IP address, and each IP address belongs to some block of contiguous IP addresses forming an identifiable unit called a prefix. Roughly speaking, a prefix specifies a block of addresses used by a single network. Prefixes are the units of routing on the Internet. Routers that shuffle packets across the Internet make their routing decisions primarily at the granularity of prefixes. Given a packet, a router first determines to which prefix the IP address of the destination host belongs, and then makes a routing decision specific to that prefix. Because prefixes are the units of routing, and because addresses making up a prefix typically belong to a single organization (unless the prefix has been further subdivided), it is reasonable to aggregate the count of infected hosts at the granularity of prefixes.
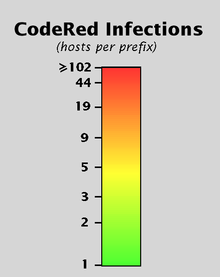
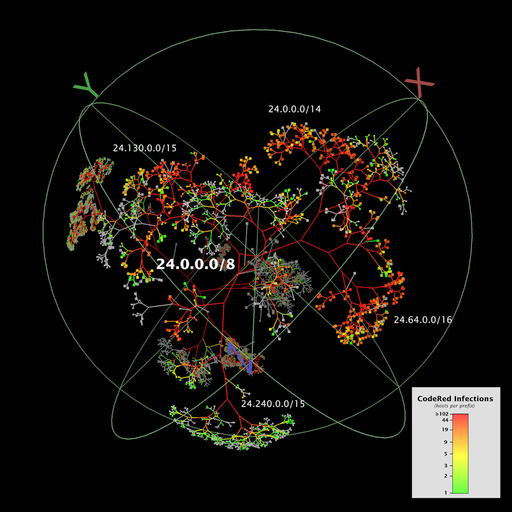
This visualization depicts the number of hosts infected by CodeRed (and variants) during the 24 hour period starting on July 19, 2001, UTC. The counts of infected hosts are aggregated at the granularity of prefixes. Each node represents a BGP prefix announced to RouteViews on July 19th. Prefixes without any infected hosts are colored grey, while prefixes with infected hosts are colored green to red on an approximately logarithmic scale according to the number of infections. Interior nodes have a count equal to the cumulative sum of their children, and links have the color of the node at the end lower down in the tree. The prefixes themselves are arranged in a binary tree representation of the 32-bit IP address space covered by the announced prefixes.
Although this Walrus screen capture shows the entire set of announced prefixes, detail is only visible in the nearest branch of the tree, which is centered on the node representing the prefix 24.0.0.0/8. The image naturally divides into two overlapping planes that are parallel to the screen of the viewer. The background plane contains relatively dark clusters of nodes that reveal little detail. The foreground plane contains the subtree that represents 24.0.0.0/8 and all its longer prefixes. This subtree is lighter in appearance than the subtrees of the background plane and occupies a large portion of the display area.
The 24.0.0.0/8 subtree prominently shows a large number of infections. This is unsurprising since 24.0.0.0/8 contains prefixes belonging to @Home, RoadRunner, and AT&T broadband services, as well as others, and these ISPs have a large base of residential and small business customers. CAIDA's analysis shows that home users and small businesses were among the most heavily infected as a class.
Visualization
The image uses the following key:
|
| [1024x1024 version] |
| [2048x2048 version] |
| [2048x2048 version with axis labels removed] |
Links
Credits
| Visualization: | Young Hyun (youngh@caida.org) |
| CodeRed Analysis: | David Moore (info@caida.org) Colleen Shannon (info@caida.org) |
| Data Analysis: | Bradley Huffaker (brad@caida.org) |
Walrus is a CAIDA tool developed with support of DARPA NGI N66001-98-2-8922, DARPA NMS N66001-01-1-8909, NSF ANI-9996248, NSF N66001-01-1-8909, and the support of CAIDA members.
CAIDA is based at the University of California's San Diego Supercomputer Center.

