Nameserver DoS Attack October 2002
CAIDA's DNS Performance Monitoring Data
Since January 2002, CAIDA has been monitoring performance of the DNS root and gTLD nameservers using NeTraMet passive monitors located at UCSD and in San Jose. We looked at the round trip time (RTT) and DNS request count (counts) observed at the UCSD NeTraMet monitor from October 5 through October 25. During this approximately three week period, the overall character of the root RTTs changed noticeably. Previously, with the exception of G root, RTT plots were fairly flat, with occasional short steps and/or spikes indicating slower performance. From our vantage point in San Diego, G root's performance typically varies.
Observations: 5 Oct through 25 Oct, 2002
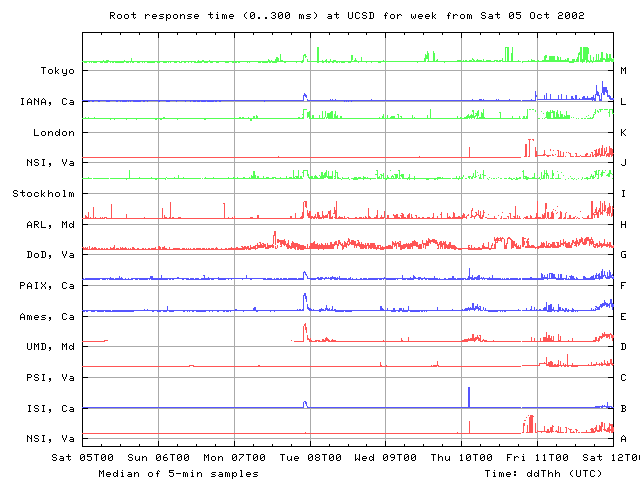
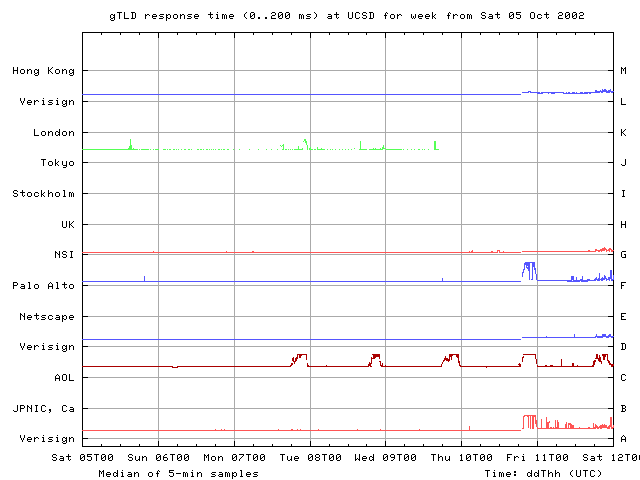
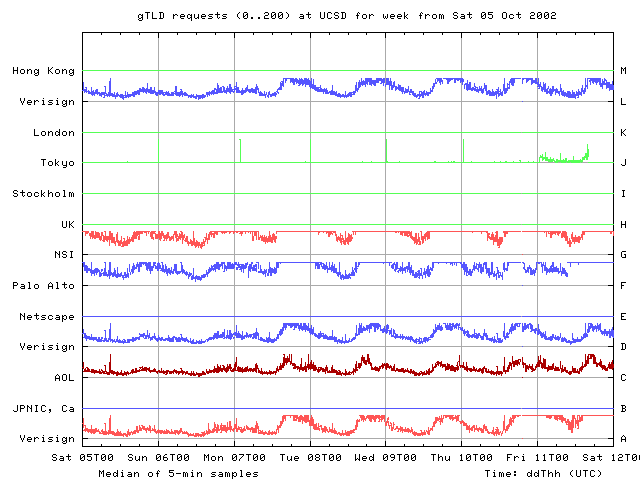
From our UCSD monitor point, the first sign of unusual behavior occurs late on 7 Oct. Performance degrades for about one hour on all roots except A, C, G, and J. On that date there is no corresponding event on the gTLDs. A fairly periodic spike seen only on the C gTLD name server beginning late 7 Oct and continuing until late 11 Oct is probably a server overload problem.
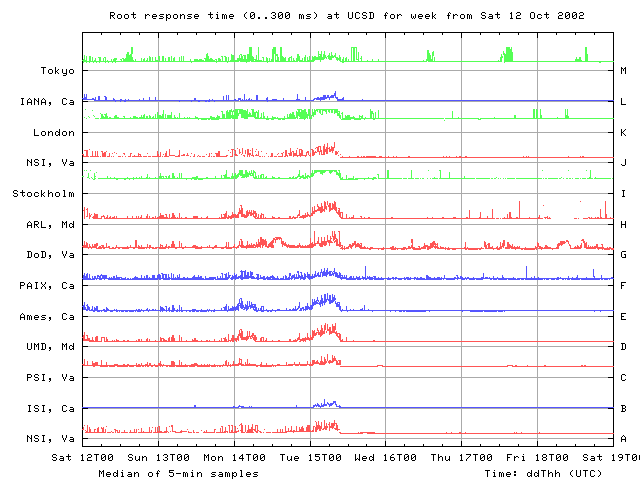
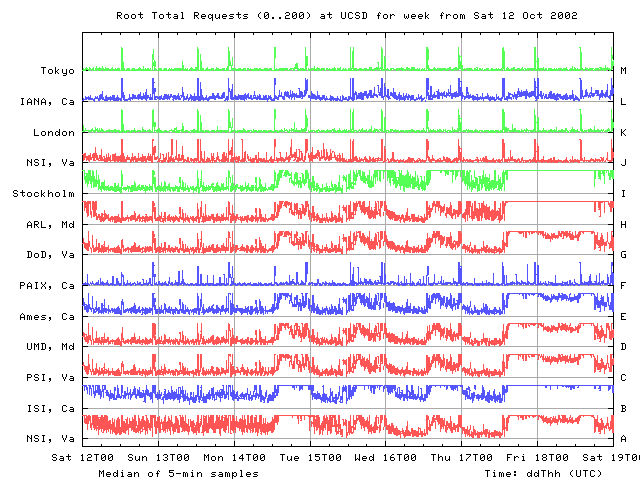
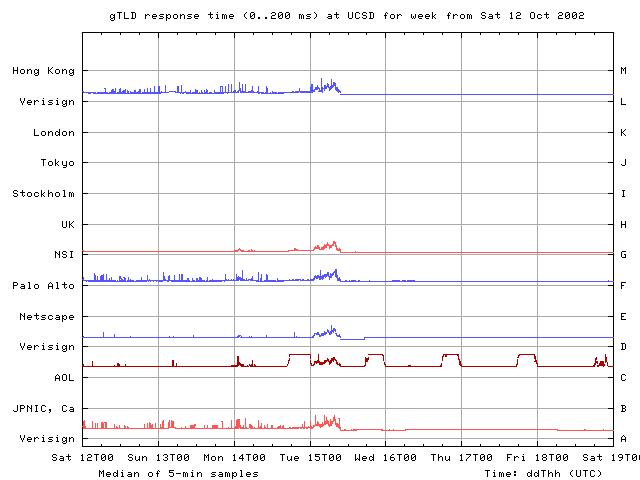
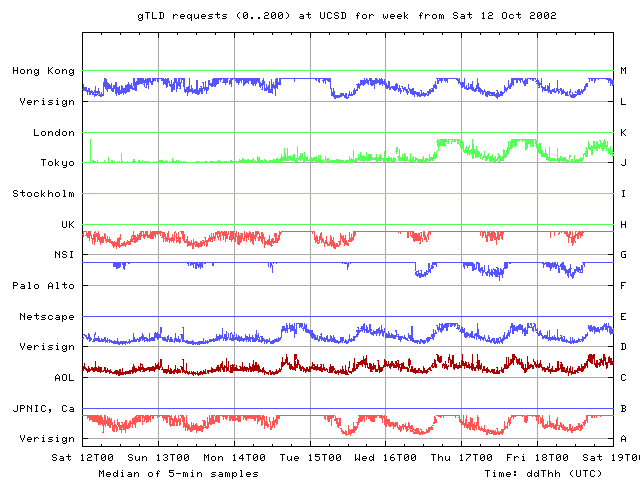
We next observed degradations in root RTTs on Saturday 12 Oct, Monday 14 Oct and Tuesday 15 Oct. RTTs rise from their individual baselines seen earlier during the previous week to significantly longer RTTs over a period of about 6 hours, then fall back to previous baselines readings in about another 3 hours. Similar performance changes are visible on all the root nameservers, though to a lesser degree on B and L roots.
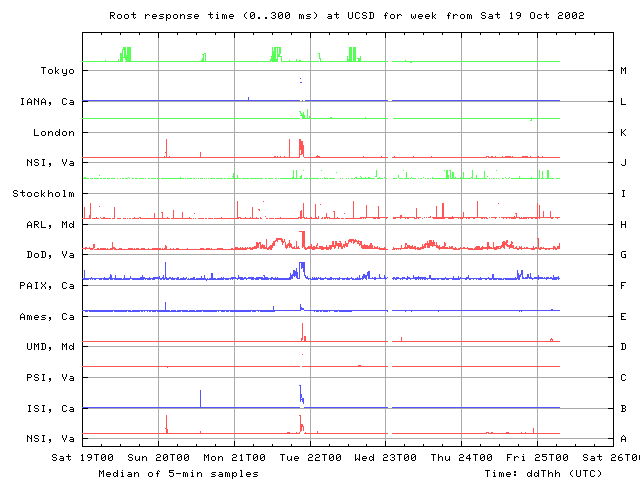
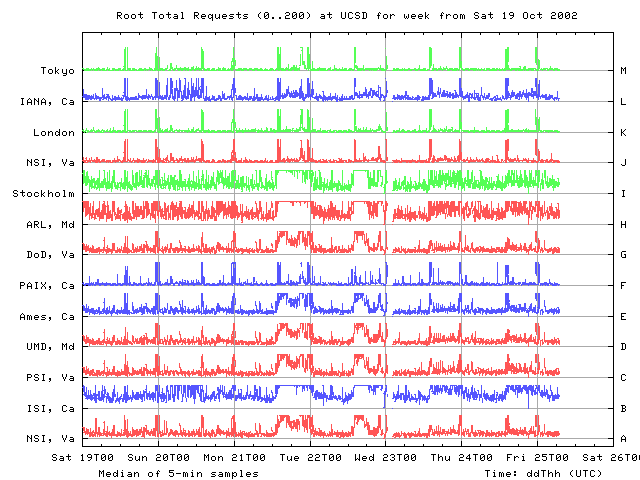
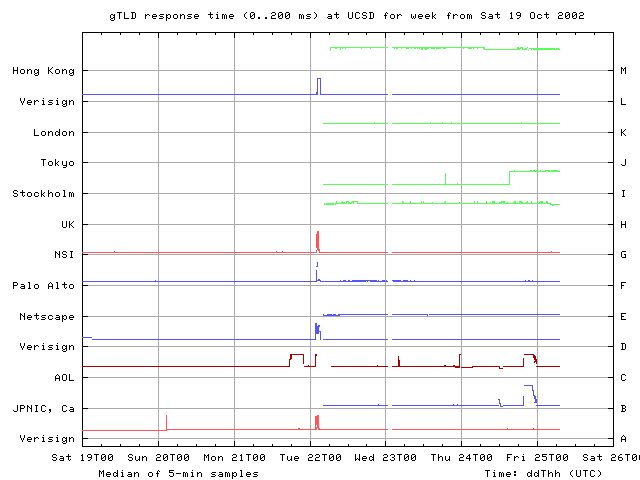
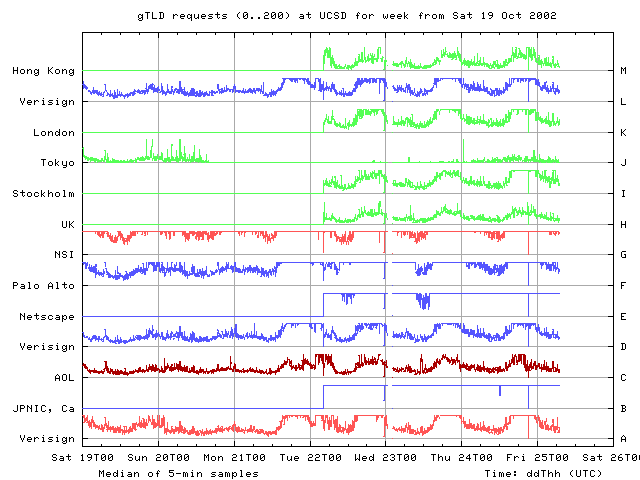
From our vantage point at UCSD, on Monday 21 Oct all root nameservers except I and M experienced degradations in performance around 2200 UTC. Within a 5 minute interval, RTTs jump from their individual normal baselines to noticeably higher levels, staying high for about an hour on F, G, and L roots, for about 5-10 minutes on B and A roots, and for a little longer than 10 minutes on J root. The gTLDs show a similar performance hit around 0100 UTC on Tuesday October 22. The attack on 15 Oct was visible on all the roots. On 21 Oct, however, no changes are seen on I and M from our UCSD monitor.
While the earlier perturbations are different from the events occurring on 21 and 22 Oct, one might speculate that the earlier degradations are consistent with behavior of someone who was testing the attack. The first sharp change on 7 Oct may have been a test of the attack, which was further developed over the next 10 days or so.
Scope and Impact of the Attack
It is worth noting that DoS attacks are an ongoing fact of life for the root nameservers as well as the rest of the Internet structure. [4] This particular Dos attack was significant enough to get media attention. Even so, the user-visible impact on global network operation was slight. (If others have data that implies differently, please let us know at info@caida.org.)
Performance Graphs
For More Information on DNS Performance Monitoring and DoS Attacks
- P. Vixie (ISC), G. Sneeringer (UMD), and M. Schleifer (Cogent). Events of 21-Oct-2002. November 24, 2002.
- D. Wessels. dnstop: a tool for detecting and filtering DNS query errors. https://www.caida.org/catalog/software/dnstop/ or http://dnstop.measurement-factory.com/.
- Plots of DNS root server and gTLD performance since January 2001 are available at https://cgi.caida.org/cgi-bin/dns_perf/main.pl.
- Analysis of the DNS root and gTLD nameserver system: status and progress report: https://www.caida.org/projects/dns/status.
- Related papers:
- N. Brownlee and I. Ziedins, "Response time distributions for global name servers", in PAM 2002, Boulder, Colorado, Mar 2002, PAM.
- N. Brownlee, k. claffy, and E. Nemeth, DNS Root/gTLD Performance Measurements", in Usenix LISA, San Diego, CA, 4-7 Dec 2001, Usenix.
- N. Brownlee, k. claffy, and E. Nemeth, "DNS Measurements at a Root Server", in Globecom, San Antonio, TX, 25-28 Nov 2001, Globecom.
- D. Moore, G. Voelker, and S. Savage. "Inferring Internet Denial-of-Service Activity" in Usenix Security Symposium, Washington, D.C., Aug 2001.